By Andrew Brandt
 Search engines appear to be no longer in control of the search results they display at any given moment. That’s bad news not only for the search giants, but for anyone who relies on their results.
Search engines appear to be no longer in control of the search results they display at any given moment. That’s bad news not only for the search giants, but for anyone who relies on their results.
How can that be? After all, it’s the search engines’ own servers that are supposed to deliver relevant results based on their super-secret sauce algorithms. But black hat, or rogue, search engine optimization (SEO for short) has ruined the trustworthiness of virtually any search.
Just a few years ago, companies began to spring up making outrageous promises about how they can get a client’s Web site ranked closer to the top of certain search results. Then the purveyors of various worms, fake alerts, and rogue antivirus products got involved, because they quickly discovered that it’s easier to convince someone to infect their own computer by clicking a search result link than to discover and implement an elaborate network vulnerability.
After all, according to our latest research, about one out of every five of surveyed Web surfers implicitly trust whatever a search engine delivers as the first page of search results every time they search.
 So, all year long, we’ve seen rogue SEO tricks used to promote malicious search results. Many of those links foist various fake antivirus programs onto unsuspecting Web surfers’ computers. The effect is almost instantaneous, as if it was automated: A breaking news story hits the Internet, and within moments, the rogues have turned their attention to pushing bad links based off of whatever keywords the story-of-the-moment might entail. That’s not really unexpected; Google Trends, for instance, makes it incredibly easy for black hat SEOs to target whatever’s hot. Searches for news as diverse as Indonesian earthquakes, elections in Iran, and the untimely deaths of various celebrities served equally well to deliver victims to the rogues.
So, all year long, we’ve seen rogue SEO tricks used to promote malicious search results. Many of those links foist various fake antivirus programs onto unsuspecting Web surfers’ computers. The effect is almost instantaneous, as if it was automated: A breaking news story hits the Internet, and within moments, the rogues have turned their attention to pushing bad links based off of whatever keywords the story-of-the-moment might entail. That’s not really unexpected; Google Trends, for instance, makes it incredibly easy for black hat SEOs to target whatever’s hot. Searches for news as diverse as Indonesian earthquakes, elections in Iran, and the untimely deaths of various celebrities served equally well to deliver victims to the rogues.
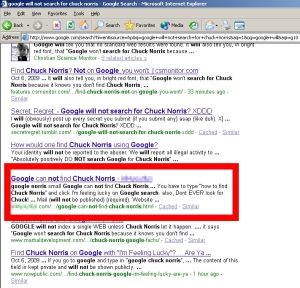
Now, even the Internet meme of the moment appears to drive victims to malicious Web pages. One of our researchers pointed out a funny screenshot that was making its way through Digg, the social link-sharing site. The screenshot showed some of Google’s suggested search results that appear when you type “Google will” into the search field. Among the auto-completions were “Google will not search for Chuck Norris,” “Google will eat itself,” and “Google will you marry me?”
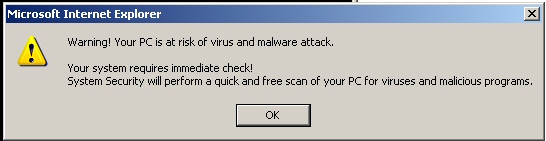
Even picking one of the most obscure searches, “Google will not search for Chuck Norris,” the eponymous results delivered malicious links not only on the first page, but one as the fourth result on the first page. That search result led directly into a fake antivirus alert page; The fake “Windows Web Security” alert immediately began displaying an animation of a “scan” — with the expected results.
The alert came from a folder that had been placed on the Web site of a real estate agent in Wilmington, North Carolina. The top level of the site was clean, but one page buried deep within the site contained a script that redirected users into a fake alert black hole. No matter where you clicked — even if you tried to close the browser — the page attempted to convince you to download and execute the installer for a rogue antivirus program. This use of hacked, legitimate Web servers, with a malicious script buried in some obscure subfolder, as the target of these “optimized” search results is another growing trend.
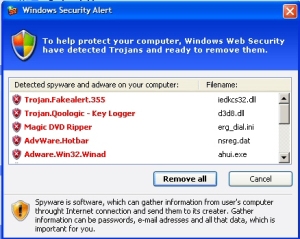
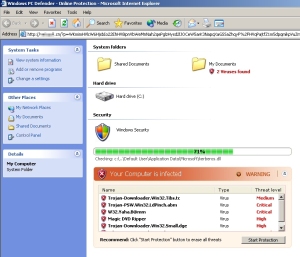
Another link on the same page led to a screenshot of the humorous Google result that, supposedly, appears when you search for Chuck Norris. But that immediately redirected the browser through a series of exploits which rapidly pushed executables down to the test machine and forced a reboot. After the test system came back up, it had a fully installed copy of the infamous Antivirus 2010, as well as an ad-clicking Trojan that, invisibly to the user, was clicking through Web advertisements hosted by Amazon, Yahoo, and Doubleclick at a rate of about 20 per second.
What does this mean for the average Web user? I think it means Google and the other search engines have a long way to go before they can really put a dent in search manipulations like these.
Tip of the (white) hat to threat research analyst Abhishek Dubey for finding something useful in a Google search for Chuck Norris.













BTW, What about Bing.com? I think there searches are safer then Google.
When will our lawmakers in Washington enact some punishing legislation with jail time for all these hackers? Why is Google allowing it’s site to be kidnapped like this?
I was doing a search on Yahoo! and ended up downloading a rogue anti-virus program called Antivirus System PRO. It has a trojan.fakeAV virus in it and gave fake AV alerts , controlled IE 8.0 in Windows 7, added registry keys, and was a bear to get rid of even with Norton Internet Security 2009 and Webroot Antivirus scanners installed. These guys behind these bogus AV programs should be tracked down, prosecuted and jailed.
Interesting information, but when was this blog started? I had worked on two computers from two different clients. The same fake anti-virus program infected the computers. “Antivirus 2009.”
Maybe you should get this information out a little quicker?
The blog started on March 23, 2009. This post was made in October, 2009. And yes, we know that this family of rogue antivirus products has been around a while. The point of this post wasn’t to alert users to the existence of this rogue — frankly, if you work in IT, you’d have to be living under a rock not to have heard of it — but to the new techniques being used to market it through manipulated search results.
Forewarned about the fake security alert, I knew to try to escape immediately without clicking on anything other than close (the “X”). When the rogue would not let me exit the program or even close Explorer, I successfully used Windows Task Manage (ctrl-alt-del) to end the application.
You can also use the key combination Alt-F4 to close the browser window without clicking anything. But your method will work as well.
OMG I go that fake software illustrated few days ago. They advised me malwarebytes but it won’t install
What should I do?
You should stop spamming blog comments with links to a rogue av product.
Pingback: Internet Security Trends – A Look Back at 2009, A Look Ahead to 2010 « Webroot Threat Blog